Quest Security and Service Advisories
As an ongoing service to Quest's valued clients, our team of experts monitors security and service advisories we are seeing in the market from multiple vendors and these important notices are sent to our clients. You can view an overview of our recent advisories below. If you need more information on any of these advisories, or would like to set up a meeting to discuss them further, please reach out to our team.

July 2024
Security Advisory: Urgent Notice: Increased Threat Actor Activity Post-Crowdstrike Outage (7/22)
Security Advisory: Crowdstrike - Official Workaround to Ongoing Issue (7/18)
Security Advisory: Critical Vulnerabilities in OpenSSH (7/2)
June 2024
Security Advisory: Critical Vulnerabilities in VMware vCenter Server (6/19)
Security Advisory: Pure Storage Cyber Incident (6/14)
May 2024
Security Advisory: Cyber Threats Targeting Snowflake Accounts (5/31)
Security Advisory: Holiday Weekend Preparation and Response for Ransomware Attacks (5/22)
Security Advisory: Critical Roll Up Patches for May (5/16)
April 2024
Security Advisory: Cisco DDoS/Code Execution Threat (4/29/2024)
Security Advisory: PAN Re-statement Recommendations
Security Advisory: Citrix: Citrix Hypervisor Security Update
Security Advisory: Palo Alto Network: CVE-2024-3400
Security Advisory: Fortinet: FG-IR-23-493 (4/9/2024)
March 2024
Security Advisory: Critical VMware Vulnerabilities Identified
February 2024
Security Advisory: ConnectWise ScreenConnect Security Threat
Security Advisory: Critical Vulnerabilities (CVSS 9.8) in Wide Range of Fortinet Software
January 2024
Security Advisory: Malware Bypassing Office 365 Filters
December 2023
Security Advisory: Advanced Phishing Attempt Posing as WordPress
Security Advisory: Google Chrome 0-Day Vulnerability
November 2023
Security Advisory: User ID Cleanup - Access Control
Security Advisory: Cisco Releases Software Updates for Multiple Vulnerabilities
October 2023
Security Advisory: Latest Threat Actor Exploits: CISA Reveals Vulnerabilities and Misconfigurations
Security Advisory: VMware vCenter Critical CVE Advisory
Security Advisory: HTTPS/2 Rapid Reset Zero Day Vulnerability
Security Advisory: Cisco Cyber Threat
September 2023
Security Advisory: Addressing the Surge in Ransomware Attacks
Security Advisory: Security Awareness Training
Security Advisory Update: Social Engineering “Password Reset Policy”
Security Advisory: End of Support for Microsoft Server OS 2012 and 2012 R2
July 2024
Security Advisory: Urgent Notice: Increased Threat Actor Activity Post-Crowdstrike Outage (7/22):
In the wake of the recent global Crowdstrike outage on July 19th, 2024, threat actors and scammers are known to exploit the situation to their advantage. We are reminding you to be vigilant to detect fake emails, voice calls, texts, and websites that pretend to be official. We are seeing an increase in threat actor malicious activity posing as technical support teams or Crowdstrike to attempt trick you to gain personal information, such as passwords, credit card numbers, or other sensitive data using Phishing (Email), Smishing (SMS Text Messages) and Vishing (Phone calls). There are also attempts to leverage a malicious ZIP archive claiming to be a hot fix.
You will never be contacted be contacted (by any means) by Crowdstrike Support directly.
This is a reminder to all of our users to remain vigilant and only follow instructions from legitimate sources. Please avoid the following communication types regarding Crowdstrike:
- Clicking on phishing emails or suspicious links
- Engaging in Phone call conversations or responding to voicemails
- Engaging in Text Message communications
- Using a Zip file that claims to be a hotfix
Common Vishing and Smishing Techniques:
Caller ID Spoofing: Attackers may manipulate caller ID to make it appear as though the call is coming from a trusted source.
Urgency and Fear: Scammers often create a sense of urgency or fear to pressure individuals into providing information quickly.
Pre-recorded Messages: Some vishing attacks use automated messages to instruct recipients to call a number and provide personal information.
How to protect yourself:
Verify the Caller: The number one thing you can do If you receive a suspicious call is to hang up and call the organization directly using a known and trusted phone number.
Do Not Share Personal Information: Never provide sensitive information over the phone especially if they called you.
Report Suspicious Calls: If you receive a vishing call, immediately report it to the IT department.
Did you miss an advisory? Check out our advisory page here: https://questsys.com/Quest-Security-and-Service-Advisories/
Security Advisory: Crowdstrike - Official Workaround to Ongoing Issue (7/18):
Tech Alert | Windows crashes related to Falcon Sensor | 2024-07-19
Cloud:
US-1EU-1US-2
Published Date: Jul 18, 2024
Summary
CrowdStrike is aware of reports of crashes on Windows hosts related to the Falcon Sensor.
Details
- Symptoms include hosts experiencing a bugcheck\blue screen error related to the Falcon Sensor.
- Windows hosts which have not been impacted do not require any action as the problematic channel file has been reverted.
- Windows hosts which are brought online after 0527 UTC will also not be impacted
- The issue is not impacting Mac- or Linux-based hosts
- Channel file "C-00000291*.sys" with timestamp of 0527 UTC or later is the reverted (good) version.
- Channel file "C-00000291*.sys" with timestamp of 0409 UTC is the problematic version.
Current Action
- CrowdStrike Engineering has identified a content deployment related to this issue and reverted those changes.
- If hosts are still crashing and unable to stay online to receive the Channel File Changes, the following steps can be used to workaround this issue:
Workaround Steps for individual hosts:
- Reboot the host to give it an opportunity to download the reverted channel file. If the host crashes again, then:
- Boot Windows into Safe Mode or the Windows Recovery Environment
- Navigate to the %WINDIR%\System32\drivers\CrowdStrike directory
- Locate the file matching “C-00000291*.sys”, and delete it.
- Boot the host normally.
- Note: Bitlocker-encrypted hosts may require a recovery key.
Workaround Steps for individual hosts:
Option 1:
- Detach the operating system disk volume from the impacted virtual server
- Create a snapshot or backup of the disk volume before proceeding further as a precaution against unintended changes
- Attach/mount the volume to to a new virtual server
- Navigate to the %WINDIR%\\System32\drivers\CrowdStrike directory
- Locate the file matching “C-00000291*.sys”, and delete it.
- Detach the volume from the new virtual server
- Reattach the fixed volume to the impacted virtual server
Option 2:
- Roll back to a snapshot before 0409 UTC.
Workaround Steps for Azure via serial:
- Login to Azure console --> Go to Virtual Machines --> Select the VM
- Upper left on console --> Click : "Connect" --> Click --> Connect --> Click "More ways to Connect" --> Click : "Serial Console".
- Once SAC has loaded, type in 'cmd' and press enter.
- type in 'cmd' command
- type in : ch -si 1
- Press any key (space bar). Enter Administrator credentials
- Type the following:
- bcdedit /set {current} safeboot minimal
- bcdedit /set {current} safeboot network
- Restart VM
- Optional: How to confirm the boot state? Run command: wmic COMPUTERSYSTEM GET BootupState
In the event that you need further assistance please contact us at or 1800-443-5605.
Did you miss an advisory? Check out our advisory page here: https://questsys.com/Quest-Security-and-Service-Advisories/
Security Advisory: Critical Vulnerabilities in OpenSSH (7/2):
Quest has been notified of a security advisory addressing critical vulnerabilities in OpenSSH, including an unauthenticated remote code execution (RCE) vulnerability dubbed "regreSSHion," which grants root privileges on glibc-based Linux systems.
Vendor: OpenSSH / Linux Based systems
CVE(s): CVE-2024-6387
CVSS: 8.1 High
Description: A signal handler race condition was found in OpenSSH's server (sshd). If a client does not authenticate within LoginGraceTime seconds (120 by default, 600 in older OpenSSH versions), sshd's SIGALRM handler is called asynchronously.
Impact: A remote, unauthenticated attacker can exploit this flaw to execute arbitrary code with root privileges, potentially leading to full system compromise.
Workarounds: None; however, Quest highly recommends the security practice of keeping SSH management interfaces on a "controlled" network, isolated/blocked from user/non-management segments.
Link to source(s):
- https://ubuntu.com/security/CVE-2024-6387
- https://explore.alas.aws.amazon.com/CVE-2024-6387.html
- https://security-tracker.debian.org/tracker/CVE-2024-6387
- https://access.redhat.com/security/cve/cve-2024-6387
The list is growing; please scan for vulnerabilities and check with your local and cloud deployments for additional susceptible platforms/instances.
Recommendation: Perform a complete vulnerability scan, review applicability, and apply the updates as soon as possible.
If you need assistance with remediation, would like to request a vulnerability scan, or would like to discuss this in more detail, please let us know.
June 2024
Security Advisory: Critical Vulnerabilities in VMware vCenter Server (6/19):
Quest has been notified of a security advisory addressing critical vulnerabilities in VMware vCenter Server, including unauthenticated remote code execution (RCE). See the details below:
Vendor: VMWare
CVE(s): CVE-2024-37079, CVE-2024-37080, CVE-2024-37081
CVSS: 9.8 Critical
Description: VMware vCenter Server updates address heap-overflow and privilege escalation vulnerabilities
Impact: An unauthenticated malicious actor, with network access to vCenter Server, may trigger these vulnerabilities by sending a specially crafted network packet potentially leading to remote code execution and root privileges.
Workarounds: None; However, Quest highly recommends the security practice to keep Vcenter management interfaces on a “controlled” network isolated/blocked from user / non-management segments.
Link to source(s): https://support.broadcom.com/web/ecx/support-content-notification/-/external/content/SecurityAdvisories/0/24453
Recommendation: Review applicability and apply the updates as soon as possible.
Security Advisory: Pure Storage Cyber Incident (6/14):
Quest has been made of aware of a cyber incident involving Pure Storage. An unauthorized third party gained access to a Snowflake data analytics workspace. For more details, please refer to the Pure Storage Documentation portal.May 2024
Security Advisory: Cyber Threats Targeting Snowflake Accounts (5/31):
Quest Security Threat Intelligence has received reports from Snowflake, which is observing and investigating an increase in cyber threat activity targeting Snowflake customers’ accounts. There are unconfirmed reports of customer data exposure of some select Snowflake customers. Snowflake believes this is the result of ongoing industry-wide, identity-based attacks with the intent to obtain customer data using poorly secured accounts. Snowflake provided Indicators of compromise to aid in threat hunting, remediation and prevention. This threat is emerging/preliminary and subject to change.
Link to additional information: https://community.snowflake.com/s/article/Communication-ID-0108977-Additional-Information
If you need assistance or would like to discuss this in more detail, please let us know, and we can schedule a meeting to review.
Security Advisory: Holiday Weekend Preparation and Response for Ransomware Attacks (5/22):
As the Memorial Day holiday approaches this weekend, it's crucial to remain vigilant with your defenses and operational monitoring of your security tools and solutions. The Federal Bureau of Investigation (FBI) and the Cybersecurity and Infrastructure Security Agency (CISA) have observed an increase in highly impactful ransomware attacks occurring on and around holidays when offices are closed and staff is reduced.
If you encounter anything abnormal or suspicious during the holiday weekend, please contact Quest Technology at . We operate a 24x7 fully staffed NOC/SOC and security practice, including an incident response team, ready to assist you.
Should you need assistance this week with any current patching, remote user access, or other immediate security tasks, please let us know before Friday. Our experts are on hand to help close any gaps before the weekend.
Again, you can reach us at , or call 800-443-5605 for any critical or suspicious activities.
Security Advisory: Critical Roll Up Patches for May (5/16):
CVE-2024-30040: CVSS 8.8 / Windows MSHTML Platform Security Feature Bypass Vulnerability *Active Exploit*
CVE-2024-30051: CVSS 8.8 / Windows MSHTML Platform Security Feature Bypass Vulnerability *Active Exploit* Qakbot is using this as an initial infection vector (via phishing email with file) for affiliates including Conti, ProLock, Egregor, REvil, RansomExx, MegaCortex, and most recently, Black Basta
CVE-2024-30046: CVSS 5.9 / Visual Studio Denial of Service Vulnerability
Recommendation: Patch urgently
Other Notables
Cisco: Cisco IP Phone 6800, 7800, and 8800 Series with Multiplatform Firmware Vulnerabilities CVE-2024-20357, CVE-2024-20376, CVE-2024-20378 – CVSS 7.5
Apple: Apple issued a security advisory that backports fixes zero-day exploited in attacks to older iPhones *Active Exploit*
- Link: https://support.apple.com/en-us/HT201222
- Please check and update your iPhone software
Chrome: Google Chrome emergency update fixes 6th zero-day exploit in 2024 *Active Exploit*
- Link: https://chromereleases.googleblog.com/2024/05/stable-channel-update-for-desktop_13.html
- Recommend: Patch urgently
April 2024
Security Advisory: Cisco DDoS/Code Execution Threat (4/29/2024):
Cisco is warning of a state-backed hacking group has been exploiting two zero-day vulnerabilities in Adaptive Security Appliance (ASA) and Firepower Threat Defense (FTD) firewalls since November 2023 to breach government networks worldwide. CVE-2024-20353 (denial of service) and CVE-2024-20359 (persistent local code execution)—that the threat actors used as zero-days in these attacks.
Vendor: Cisco
CVE(s): CVE-2024-20353, CVE-2024-20359, CVE-2024-20358
CVSS: 8.6, 6.0 High
Description: DDoS / Code execution
Impact: Observed in attacks, configuration modification, reconnaissance, network traffic capture/exfiltration and potentially lateral movement
Link to source(s):
1. CVE-2024-20358 - https://sec.cloudapps.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-asaftd-cmd-inj-ZJV8Wysm
2. CVE-2024-20359 - https://sec.cloudapps.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-asaftd-persist-rce-FLsNXF4h
3. CVE-2024-20353 - https://sec.cloudapps.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-asaftd-websrvs-dos-X8gNucD2
Additional information: https://sec.cloudapps.cisco.com/security/center/resources/asa_ftd_attacks_event_response
Recommendation: Review applicability; update to fixed release
Cisco is strongly urging its customers to patch for these vulnerabilities. Please contact Quest ASAP at (800) 326-4220 if you need our assistance. If the Quest SOC has already been in touch with you about the your managed firewalls, please ignore this message.
Security Advisory: PAN Re-statement Recommendations (4/19/2024):
Earlier this week Quest published a security advisory for a PAN vulnerability (CVE-2024-3400). Palo Alto updated guidance on this issue.
Updated:
https://security.paloaltonetworks.com/CVE-2024-3400
https://unit42.paloaltonetworks.com/cve-2024-3400/
In earlier versions of this advisory, disabling device telemetry was listed as a secondary mitigation action. Disabling device telemetry is no longer an effective mitigation. Device telemetry does not need to be enabled for PAN-OS firewalls to be exposed to attacks related to this vulnerability.
Palo Alto’s recommendation (if confirmed compromised) is to be sure to wipe the device and rebuild to a patched version; if logs tell you when the exploit took place; you can restore a base configuration prior to that date.
Added to the change is the version level (see below). Please notice the lower version of the most recent advisory (10.2.0):
- First advisory affected devices:
- Must be running GP and telemetry, and on version 10.2.9 or higher
- Second advisory affected devices:
- Must be running GP, and on version 10.2.0 or higher.
Security Advisory: Citrix: Citrix Hypervisor Security Update (4/11/2024):
Two issues have been identified that affect XenServer and Citrix Hypervisor. Each issue may allow malicious, unprivileged code in a guest VM to infer the contents of memory belonging to its own or other VMs on the same host.
For more detail, the official notification can be found here:
https://support.citrix.com/article/CTX633151/xenserver-and-citrix-hypervisor-security-update-for-cve202346842-cve20242201-and-cve202431142
Security Advisory: Palo Alto Network: CVE-2024-3400 (4/17/2024):
A command injection vulnerability in the GlobalProtect feature of Palo Alto Networks' PAN-OS software, for specific PAN-OS versions and distinct feature configurations, may enable an unauthenticated attacker to execute arbitrary code with root privileges on the firewall. For more detail, the official notification can be found here: https://security.paloaltonetworks.com/CVE-2024-3400Security Advisory: Fortinet: FG-IR-23-493 (4/9/2024):
An insufficiently protected credentials vulnerability (CWE-522) in FortiOS and FortiProxy may allow an attacker to obtain the administrator cookie under rare and specific conditions, by tricking the administrator into visiting a malicious, attacker-controlled website through SSL-VPN. For more detail, the official notification can be found here: https://www.fortiguard.com/psirt/FG-IR-23-493March 2024
Security Advisory: Security Advisory: Critical VMware Vulnerabilities Identified (3/8/2024):
VMware has released updates to address multiple security vulnerabilities in VMware ESXi, Workstation, and Fusion. These vulnerabilities are critical and require immediate attention.
Please let us know if you would like to discuss the new CVEs or need assistance with patching these vulnerabilities.
Impact:
A malicious actor with local administrative privileges on a virtual machine can exploit these vulnerabilities to execute code as the virtual machine's VMX process running on the host. This could result in devastating code execution on machines where Workstation or Fusion is installed or contained within the VMX sandbox on ESXi.
Impacted Products:
- VMware ESXi
- VMware Workstation Pro / Player (Workstation)
- VMware Fusion Pro / Fusion (Fusion)
- VMware Cloud Foundation (Cloud Foundation)
Vulnerabilities Summary:
- CVE-2024-22252: Use-after-free vulnerability in XHCI USB controller. Critical severity with a maximum CVSSv3 base score of 9.3 for Workstation/Fusion and 8.4 for ESXi.
- CVE-2024-22253: A use-after-free vulnerability in the UHCI USB controller. It is critical, with a maximum CVSSv3 base score of 9.3 for Workstation/Fusion and 8.4 for ESXi.
- CVE-2024-22254: Out-of-bounds write vulnerability in VMware ESXi. High severity with a CVSS score of 7.9.
- CVE-2024-22255: Information disclosure vulnerability in UHCI USB controller affecting VMware ESXi, Workstation, and Fusion.
February 2024
Security Advisory: ConnectWise ScreenConnect Security Threat (2/22/2024):
Quest has been made aware of a significant and active cyber threat affecting ConnectWise ScreenConnect. Known vulnerabilities present a maximum security risk in ScreenConnect version 23.9.8 or prior, allowing threat actors to gain remote unauthenticated access to the ScreenConnect Platform. While ScreenConnect cloud servers hosted on screenconnect.com, hostedrmm.com, or those part of Quest Services are already secured against potential attacks, partners using a dedicated on-premise ScreenConnect Platform are advised to update their ScreenConnect to version 23.9.8 immediately.
Quest recommends that our customers and partners review the applicability of this update and upgrade to the latest version of ScreenConnect as necessary.
For more detail, the official notification can be found here:
https://www.connectwise.com/company/trust/security-bulletins/connectwise-screenconnect-23.9.8
If you need help applying the necessary recommendations, reviewing for malicious activity, or would like to discuss further, we are here to help.
Security Advisory: Critical Vulnerabilities (CVSS 9.8) in Wide Range of Fortinet Software (2/9/2024)
Quest has been made aware of multiple, significant Cyber threats affecting Fortinet devices running a wide range of ForitOS software. The vulnerabilities, when exploited, could allow threat actors to execute remote code on the affected devices, perform denial of service attacks and establish a Man-in-the-Middle presence between multiple Fortinet devices. The CVSS (Common Vulnerability Scoring System) score for the most significant of these vulnerabilities is a Critical 9.8 (out of 10) and subsequently Quest is recommending that our customers immediately patch their devices to the appropriate level. Affected versions of FortiOS software are as follows: FortiOS versions: 6.0, 6.2, 6.4, 7.0, 7.2, 7.4, and 7.6 FortiProxy versions: 7.0, 7.2, and 7.4. A summary of the vulnerabilities, along with technical detail can be found here: https://www.cisecurity.org/advisory/multiple-vulnerabilities-in-fortios-could-allow-for-remote-code-execution_2024-019 If you would like to discuss this further or if you have any other questions, we are here to help.January 2024
Security Advisory: Malware Bypassing Office 365 Filters (1/12/2024):
Quest has been actively investigating the surge in phishing and malware attacks that cleverly evade third-party gateway filters. These attacks are bypassing defenses and delivering malware directly to Office 365 mailboxes. The Threat actors exploit the default MX records associated with onmicrosoft.com domains, typically taking the form of "CompanyName.onmicrosoft.com," to deliver spam and malicious content without being scanned.
Advanced configuration is required, which may impact mail flow from SMTP devices (printers, scanners, applications) that send mail directly into Office 365 from on-premise locations. Careful deployment and tuning are necessary to ensure minimal interruption to mail flow.
Quest is offering a 30-minute conversation to discuss this threat in greater detail and review options/strategy to close this possible bypass on your office365 tenant. Please reply to this email if you would like to schedule time to discuss details and options for review and remediation.
December 2023
Security Advisory: Advanced Phishing Attempt Posing as WordPress (12/5/2023):
Quest has been made aware of an advanced phishing attempt that appears to come from “WordPress”. The phishing attempt claims there is an active WordPress vulnerability requiring immediate action. The fraudulent email includes a malicious “patch” download link, which is a near duplicate of the actual WordPress site. When downloaded and installed, this "patch" creates a hidden administrative account and establishes persistence on the affected host. This allows threat actors to connect remotely and perform administrative functions at will.
Images of the email and download site are provided below:
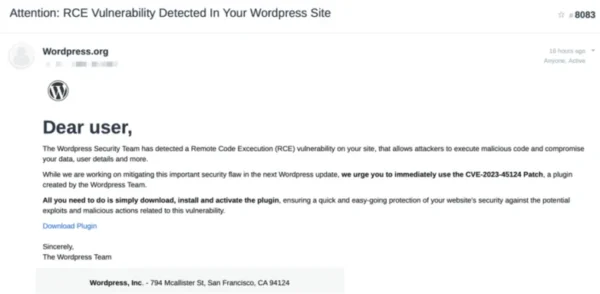
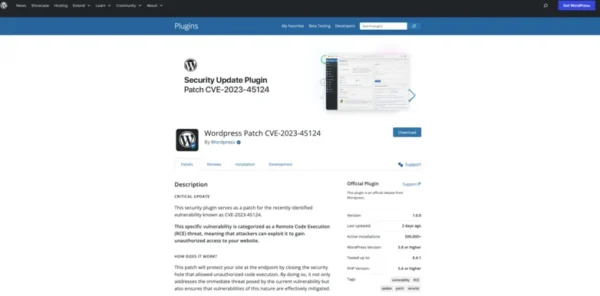
Quest recommends that our customers remain vigilant and verify any advisories through multiple sources such as CISA.gov or by manually visiting the vendor’s advisory sites.
More information can be found here: https://www.bleepingcomputer.com/news/security/fake-wordpress-security-advisory-pushes-backdoor-plugin/ Alternatively, by contacting Quest, our security experts can assist in identifying potential phishing attempts and help you stay ahead of threats to your environment. If you wish to discuss this further, we are here to help.Security Advisory: Google Chrome 0-Day Vulnerability (12/1/2023):
Quest has been made aware of a significant Cyber threat affecting Google’s Chrome browser. This vulnerability, currently rated a High severity by NIST and actively being exploited, affects versions of Chrome prior to 119.0.6045.199. Threat actors can craft custom web pages that, when accessed, execute malicious code on the host system allowing for access to sensitive data and/or other malicious activity. Quest recommends that our customers immediately patch all versions of Chrome to latest available update. More information on the vulnerability can be found below: https://nvd.nist.gov/vuln/detail/CVE-2023-6345 https://www.darkreading.com/vulnerabilities-threats/google-patches-another-chrome-zero-day-as-browser-attacks-mount If you need help applying the necessary recommendations, staying on top of patching within your environment, reviewing your environment for malicious activity, or would like to discuss further, we are here to help.November 2023
Security Advisory: User ID Cleanup - Access Control (11/21/2023):
Threat actors continue to succeed by targeting user access to systems such as Active Directory (AD), Software as as Service (SaaS) applications, partner portals, and client applications. A successful breach grants a hacker access to a user's computer, your network, direct access to cloud systems like email, and enable them to streamline their harmful activities, compromising both on-site and off-site applications and data. There are a few ways you can protect yourself from these targeted attacks, which we have outlined below:
- Conduct Auditing and Monitoring on a Scheduled Basis: Audit user and admin accounts for inactive or unauthorized accounts quarterly. Prioritize the review of remote monitoring and management accounts that are publicly accessible — this includes audits of third-party access given to service providers. Monitoring user activities, especially those with elevated permissions, can help detect and neutralize suspicious activities swiftly.
- Don't Overuse Elevated Privileges: If attackers compromise an account with elevated privileges, the results can be devastating. Implement the principle of least privilege, minimizing the number of users with elevated privileges. Restrict and monitor the activities of accounts associated with the Domain Admins group or Enterprise Admins group.
- Implement Multi-Factor Authentication (MFA): Implement phishing-resistant MFA for all services, particularly for email, VPNs, and accounts that access critical systems. Escalate to senior management upon the discovery of systems that do not allow MFA, systems that do not enforce MFA, and any users who are not enrolled with MFA.
- Lockout Policies: Enforce account lockout policies after a certain number of failed login attempts. Log and monitor login attempts to detect brute force password cracking and password spraying.
- Create and Follow Off-Boarding Practices to Remove All Application Access: Collaborate with business units and IT to remove user access to AD, SaaS, Client, and Partner systems.
- Save Money: Establishing good access management and off-boarding practices will reduce the expenses to your organization by eliminating payment for services that are no longer needed.
Security Advisory: Cisco Releases Software Updates for Multiple Vulnerabilities (11/3/2023):
Cisco recently released software updates to address an extensive range of over 25 vulnerabilities across several Cisco products, including the Adaptive Security Appliance (ASA), Firepower Management Center (FMC), and Firepower Threat Defense (FTD). This week alone, there have been 13 advisories with a rating of Critical or High impact.
The application of these updates is crucial in maintaining the security and integrity of your systems. We strongly urge all our clients to review these advisories and implement the recommended updates promptly. For more details, the official notification can be found here: Security Advisories (cisco.com) Cisco Releases Security Advisories for Multiple Products | CISA Should you require assistance in applying these recommendations, conducting a review for potential malicious activity, or if you wish to delve deeper into this matter, please reply to this email.October 2023
Security Advisory: Latest Threat Actor Exploits: CISA Reveals Vulnerabilities and Misconfigurations (10/31/2023):
The Cybersecurity and Infrastructure Security Agency (CISA) has recently published a list of known open and misconfigured ports which are frequently exploited by threat actors to gain unauthorized access to networks. These vulnerable ports allow threat actors to bypass your firewall, resulting in direct access to your platforms. Quest strongly advises our clients to conduct a comprehensive review of both inbound and outbound firewall rules. This will help identify and rectify any potential vulnerabilities, thereby minimizing the risk of cyber threats.
Most Common ports: Misconfigurations and Weaknesses Known to be Used in Ransomware Campaigns | CISA Full list of ports: Known Exploited Vulnerabilities Catalog | CISA If you need assistance in reviewing your configuration or have any questions about mitigating these risks, please contact us. Our team of experts is ready to guide you through this process and ensure the optimal security of your network infrastructure.Security Advisory: VMware vCenter Critical CVE Advisory (10/26/2023):
VMware has released a Security Advisory with a Critical rating, which affects VMware vCenter Server and VMware Cloud Foundation. An out-of-bounds write (CVE-2023-34048) and a partial information disclosure (CVE-2023-34056) pose significant risk to virtual infrastructure and data security. We highly advise all customers to promptly act to remediate these vulnerabilities by applying the updates available from VMware.
Link to VMware Advisory: https://www.vmware.com/security/advisories/VMSA-2023-0023.html If we are not already working with you to update your systems, please contact us via phone or email to schedule a meeting to review your VMware circumstances.Security Advisory: HTTPS/2 Rapid Reset Zero Day Vulnerability (10/18/2023):
Starting last week, a coordinated Denial of Service (DoS) announcement was made by Amazon Web Services, Cloudflare, and Google. They reported mitigating attacks reaching 155 million requests per second (Amazon), 201 million rps (Cloudflare), and a record-breaking 398 million rps (Google).
This vulnerability allows a remote attacker to perform a DoS attack. It exists due to improper control over the consumption of internal resources when handling HTTP/2 requests with compressed HEADERS frames. A remote attacker can send a sequence of compressed HEADERS frames followed by RST_STREAM frames to perform a DoS attack, also known as "Rapid Reset". Note that this vulnerability is being actively exploited in the wild. The resolution process involves completing discovery on all internet and internal devices running Microsoft and patching the servers, laptops, and workstations with the latest monthly patch. The key will be to ensure that all devices accessible from the internet (websites, file sharing, etc.) are discovered. For more detail, the official notification can be found here: https://www.cisa.gov/news-events/alerts/2023/10/10/http2-rapid-reset-vulnerability-cve-2023-44487 If you need help applying the necessary recommendations, need assistance with a vulnerability scan, or would like to discuss further, we are here to help.Security Advisory: Cisco Cyber Threat (10/17/2023):
Quest has been made aware of a significant Cyber threat affecting all Cisco devices running IOS XE. A known vulnerability in all versions of IOS XE with a CVSS score of 10.0, allows threat actors to gain unauthenticated access via the web UI (direct browser management) and create local admin accounts (with level 15 access). Once the account is created, the device is fully compromised allowing threat actors to immediately modify configuration, shut down services, steal credentials/configuration or gain persistence within an environment. It is believed that many Cisco devices have this feature enabled by default.
Quest recommends that our customers determine which of their devices is running Cisco IOS-XE and immediately disable the web UI on all external and internal devices. For more detail, the official notification can be found here: https://sec.cloudapps.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-iosxe-webui-privesc-j22SaA4z If you need help applying the necessary recommendations, reviewing for malicious activity, or would like to discuss further, we are here to help.September 2023
Security Advisory Update: Addressing the Surge in Ransomware Attacks (9/29/2023):
Quest continues to observe an escalation in ransomware attacks and ongoing threats. The ever-changing nature of cyber threats, coupled with the rise in zero-day vulnerabilities, amplifies the risk of falling to ransomware. In response to this evolving landscape, the Cybersecurity and Infrastructure Security Agency (CISA) frequently updates its cybersecurity alerts and advisories. We've highlighted some recent ones for your awareness and preparedness. NSA, FBI, CISA, and Japanese Partners Release Advisory on PRC-Linked Cyber Actors | CISA People's Republic of China-Linked Cyber Actors Hide in Router Firmware | CISA #StopRansomware: Snatch Ransomware | CISA Understanding the gravity of these threats, Quest has developed a set of security check-ups that align with the CISA's proactive measures. These check-ups, which can be found at https://lp.questsys.com/cybersecurity-checkups-details, are simple, quick to implement, and highly effective in warding off ransomware attacks. Please don't hesitate to reach out if you have any queries or if you require assistance in completing a security check-up. Our team is ready to assist you in fortifying your defenses against these ever-evolving cyber threats.Security Advisory Update: Security Awareness Training (9/21/2023):
October 2023 is officially recognized as Cybersecurity Awareness Month, and Quest is dedicated to spreading the word about the importance of cybersecurity awareness training. While some may initially perceive it as a gimmick, this initiative is officially sponsored by the Cybersecurity & Infrastructure Security Agency (CISA). (https://www.cisa.gov/cybersecurity-awareness-month) Security and IT professionals have consistently urged users to report any suspicious activities they encounter. In line with these efforts, our objective is to educate users on how to identify and respond to security threats effectively. We support these initiatives and encourage our clients to spend time with us, exploring how we can assist in enhancing your company's security awareness. Here's an example program for the month that illustrates how we can help:- Collaborate with clients to craft a company-wide email that breaks down the cybersecurity risks you face, how to identify them, and what steps to take upon spotting suspicious activities (such as reporting to the Help Desk or using the 'phishing email' button).
- Host a company-wide webinar discussing cybersecurity awareness, featuring real-life examples of ransomware attacks and their impact.
- Implement a cybersecurity awareness training module for new hires in your company.
- Assist clients in challenging their companies throughout October to establish or improve their email phishing scores.
