
To meet today’s ever-expanding range of digital needs, cloud capabilities are available in many flavors as enterprises move into a cloud-first mode that includes working with two or more cloud providers — something that 81% of public cloud users say they’re already doing.
Three as-a-service approaches have emerged as the cloud platforms on which multi-cloud driven digital transformations are being conducted — what analyst firm Gartner refers to as “the cloud platform continuum”:
- Software as a Service (SaaS) is typically delivered via web browser and doesn’t usually require client-side downloads.
- Infrastructure as a Service (IaaS) enables self-service accessing and monitoring of highly scalable and automated infrastructure-related capabilities and can be purchased on-demand and as-needed.
- Platform as a Service (PaaS) delivers a separate, developer-ready framework designed for building and testing apps to reduce application development overhead.
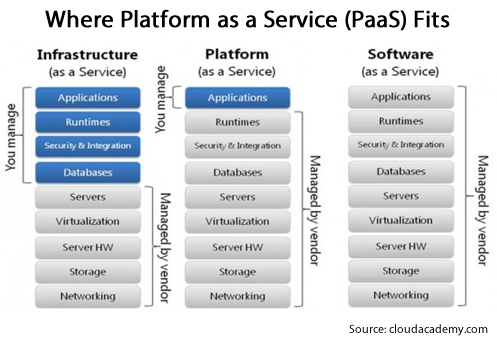
Going native with PaaS
Of course, the more your clients’ organizations embrace the use of cloud platforms to improve competitiveness, the more they’ll need to commit to cloud-native capabilities — which feature agility, speed, and continuous innovation.
Once your clients understand their need for cloud-native apps, they’ll come face to face with the impacts of complexity — multi-cloud complexity (think data security, monitoring challenges, migrating workloads, etc.) and application development complexity in particular, since both affect application architectures and software development.
PaaS addresses such complexities by delivering new levels of modularity, flexibility, security, and resilience. Consistent, predictable, and secure PaaS environments enable developers to deploy and run apps in production, at scale, via a unified self-service model that simplifies a highly complex set of IT functionalities and supports continuous delivery.
Currently available from hundreds of vendors across some 21 service categories — and growing — PaaS offerings abstract and automate cumbersome, repetitive, and error-prone development tasks, boosting app development speeds and quality.
PaaS providers manage the software development infrastructure: runtime, middleware, operating system, virtualization, servers, storage, and networking. PaaS development tools can be customized, and the software that developers create can be managed either by them or their PaaS provider.
Which PaaS is right for your clients?
As your clients contemplate which PaaS offering is best for their needs, point out to them that in this age of digital transformation, everything is a moving target — including software development platforms — and vendor lock-in is a real risk.
That’s why I suggest you help them seek out an open-source PaaS where the emphasis is on application portability and auto-scaling (horizontally and vertically), centralized platform administration and logging (including integration with external logging components), infrastructure security, dynamic routing, application health management, role-based access for deployed applications, and support for multiple IaaS providers.
And if you or your clients are even a little unsure about which path to PaaS is best for them, seek advice from a vendor-neutral technology advisor with strong PaaS experience.

