
Cloud computing that involves processing sensitive or regulated data in shared environments needs extra scrutiny in terms of security (as well as codifying requirements, defining a cloud services contract, managing the transition from in-house to cloud, and overseeing the resulting mixed IT environment).
Cloud security is at risk when…
- You don’t have an adequate cloud-oriented governance/risk/compliance framework,
- The hypervisors in your virtualized infrastructure harbor vulnerabilities that can be exploited,
- It’s possible to infer information about one virtual machine by observing the state of the shared system from another aspect of the underlying system — which might enable malicious code execution, or
- When vulnerabilities are introduced by incorrect configuration of a hypervisor and/or its related tools.
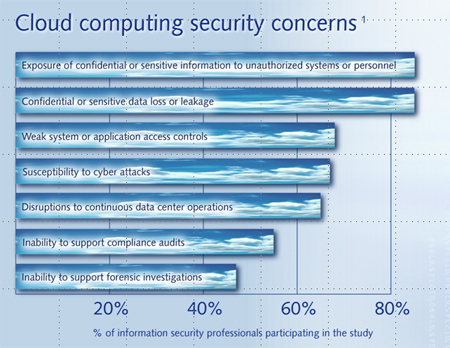
The Frost & Sullivan study from which these figures come shows a widespread belief — held by 73% of the study’s North American participants — that new skills are required for secure cloud computing. What skills? A detailed understanding of cloud computing, enhanced technical knowledge, and contract negotiation skills.
Yet for all the fear about lack of cloud security, the truth is that classic siloed IT environments are so complex, cumbersome, and riddled with years of undocumented changes that visibility is a real, serious issue. By contrast, cloud infrastructures built with virtualization technologies — and just about all clouds are built on virtualization — provide greater visibility than legacy IT environments.
Which means, ultimately, that it’s actually easier and more cost-effective to secure cloud environments than legacy IT environments.
The 2011 (ISC)2 Global Information Security Workforce Study, Frost & Sullivan
