Let’s face it: cybersecurity incident response needs all the help it can get.
One study found that 44% of those queried suffered at least twice at the hands of the same attacker, and 77% of those sufferers noted that the attacker had returned with the same or similar tactics, techniques, and procedures.
Little wonder, since 77% of organizations lack a proper incident response plan. A majority of security pros say the average incident resolution time has increased in the past year, and 42% acknowledge that their enterprises ignore a significant number of security alerts because they can’t keep up with the volume.
To the deluge of alerts and false positives, add in today’s increasingly complex and targeted cyberattacks, use of too many tools from too many vendors, incident response that remains too manual and too reactive, and very demanding compliance requirements.
You may be tempted to throw up your hands and run screaming from the building, but I have an alternative: automation.
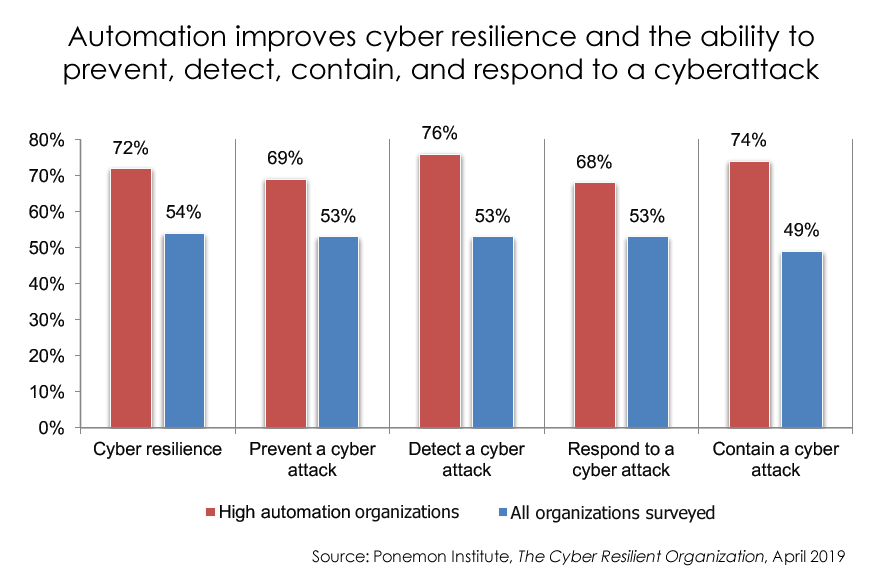
What automation can do for incident response
When automation technologies — artificial intelligence, machine learning, analytics, and orchestration — are incorporated into cybersecurity efforts, you can…
- More effectively prevent cyberattacks (and business disruption) by shortening the time needed to identify and contain an incident;
- Maximize the powerful benefits of threat intelligence sharing;
- Reduce IT infrastructure complexity while deploying the most appropriate mix of security solutions and technologies; and
- Use privacy requirements to support cyber resilience, especially as the European Union’s GDPR and the California Consumer Privacy Act are enforced.
Helping SIEM and incident response SOAR
Bringing automation to incident response involves an ongoing effort rather than a boxed product you can plug in and walk away from.
Whether you undertake this yourself or bring in cybersecurity experts to help you, the idea is to deploy security orchestration/automation/response (SOAR) technologies that aggregate data from a range of sources — chiefly security information and event management (SIEM) systems — and apply workflows aligned to processes and procedures.
Using integrations with other technologies, these workflows handle repetitive tasks, can be orchestrated into dynamic incident response playbooks that adapt in real time, and enable automatic incident escalation and remediation.
Because this SIEM and SOAR combo — generally implemented in a Security Operations Center environment (yours or your managed security services provider’s) — centralizes collection, aggregation, deduplication, and enrichment of cybersecurity data, it helps prioritize security operations, improves visibility, and reduces time to respond, contain, and remediate incidents.
There’s more, too. Talk to your trusted cybersecurity technology partner about the best way to bring automation to your incident response. Your bottom line will thank you.
Until next time,
Tim


